Cryptography System for Wireless Charging Modules
This technology secures power transfer between compliant wireless chargers and devices. Through public authentication key protocol, this technology can provide wireless power to multiple devices at once, such as in Internet of Things (IOT) applications.
Researchers
-
detuning for a resonant wireless power transfer system including cryptography
United States of America | Granted | 10,651,687 -
detuning for a resonant wireless power transfer system including cryptography
Patent Cooperation Treaty | Published application
Figures
Applications
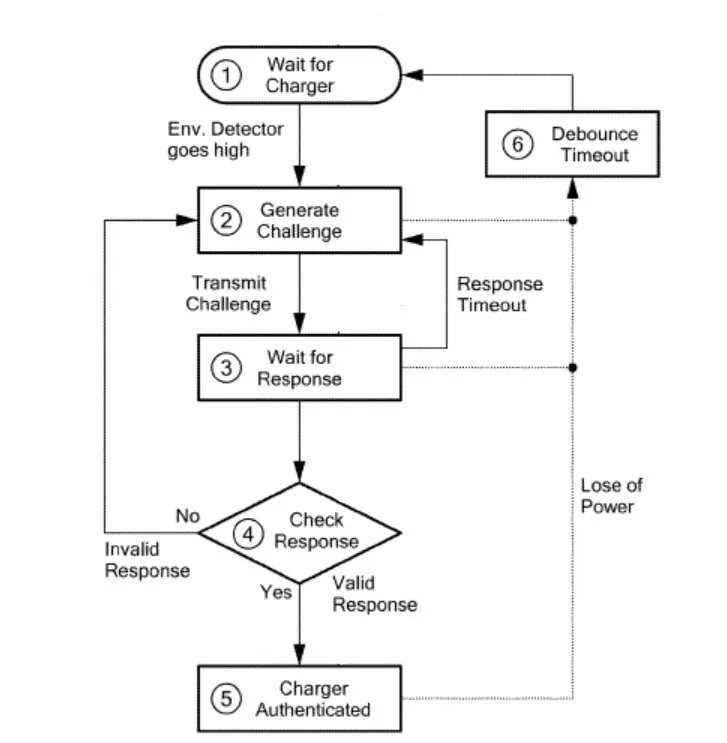
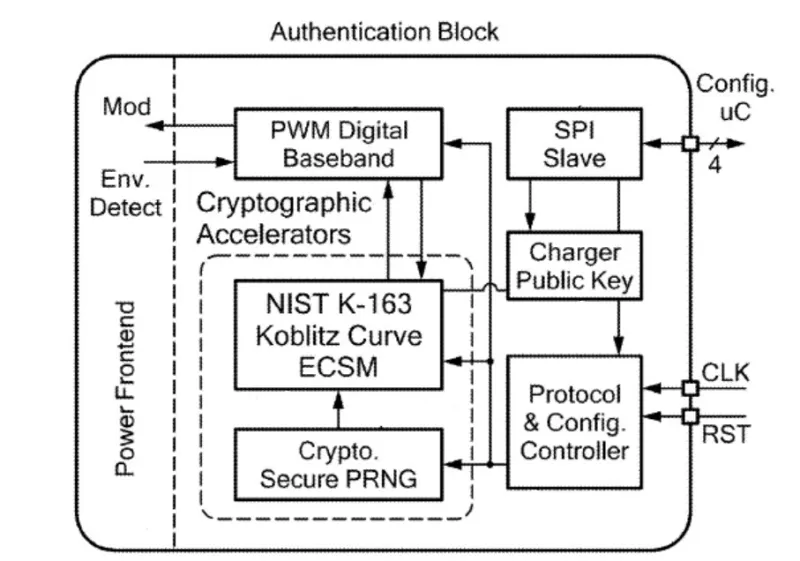
This technology employs a cryptography method that validates access keys in order to allow charging between wireless receivers and compliant chargers. The cryptography method follows a public authentication key protocol, where a receiver stores multiple public keys and a charger stores a single private key. If one of its public keys pairs with a charger’s private key, the receiver establishes a secure connection and begins the wireless power transfer process. A receiver also contains an envelope detector, which determines if the receiver is in proximity to the charger for successful power transfer.
Problem Addressed
Coupled inductors enable wireless recharging of personal electronics, wearable technologies, and IOT devices. Counterfeit wireless chargers that do not fulfil power specs of a device can send harsh transient signals, causing damage in the device’s battery and surrounding hardware. Secure hash algorithm (SHA) authentication protocols have been used to avoid charging problems between a charger-device pair. Unfortunately, these security protocols are not suitable for IOT systems, where a charger supplies power to multiple receivers.
Advantages
- Secure wireless power transfer
- Wirelessly charge multiple devices using one compliant charger
License this technology
Interested in this technology? Connect with our experienced licensing team to initiate the process.
Sign up for technology updates
Sign up now to receive the latest updates on cutting-edge technologies and innovations.